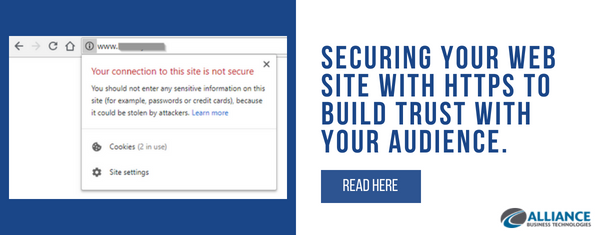
Securing your Web Site with HTTPS to build trust with your audience.
Chrome web browser is now marking all HTTP sites as "not secure". Chrome used to display a neutral information icon, but starting with version 68, the browser will warn users with an extra notification in the address bar. Chrome currently marks HTTPS-encrypted sites with a green lock icon and "Secure" sign. Google has been nudging users away...