How can we help protect you?
The security landscape continually changes. New vulnerabilities and threats are discovered all the time. It is important for you to know that you can rely on ABT to protect you as well as possible.
It is a little bit like protecting your home. 100% guaranteed security is impossible, but if you take all the recommended precautions (lock all your doors and windows with proper locks, have a working alarm system (or a noisy dog) and leave a light on if you go away for a while) you may just have enough deterrent for someone with bad intentions to skip your house.
Data and Information security is no different. Some of the mitigation strategies you can use are:
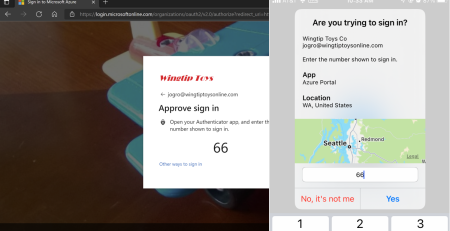
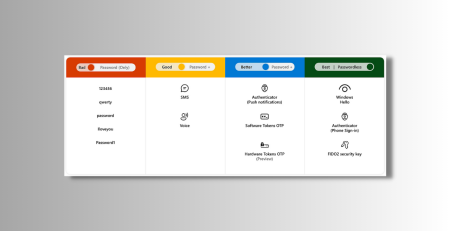
- Ensure Multi-Factor authentication is enabled and use it.
- Have a strong password that you do not use in multiple places.
- Let us manage Microsoft Windows Updates on your workstation so it is kept up to date.
- Always make sure an email is from a trustworthy sender.
- Never click on a link in an email asking you to log in to something.
- Make sure your important data is always backed up.
- Limit the third party and internal administrative accounts on your network.
- Use a VPN (Virtual Private Network) to connect to the office when you work remotely.
- Do not use public Wi-Fi when you are connecting to company resources.
- Stay away from “Social Logins”, for example where Facebook allows you to log in to a service giving the service access to your data and email.
- Use a password manager to store all your credentials, rather than saving them in your browser.
- Limit revealing personal info on social media. The posts where people share their first concert, favourite restaurant, the name of their pet and where they met their significant other may be interesting to see for their friends, but it also provides data that can be used to access accounts.
Our security specialists can assist you with performing an extensive security audit on your systems to reveal vulnerabilities you probably were not aware of. Preventing information breaches to occur is better than going through the very costly remediation and restoration required after a breach.