Securing Digital Identity: Enabling Passwordless MFA
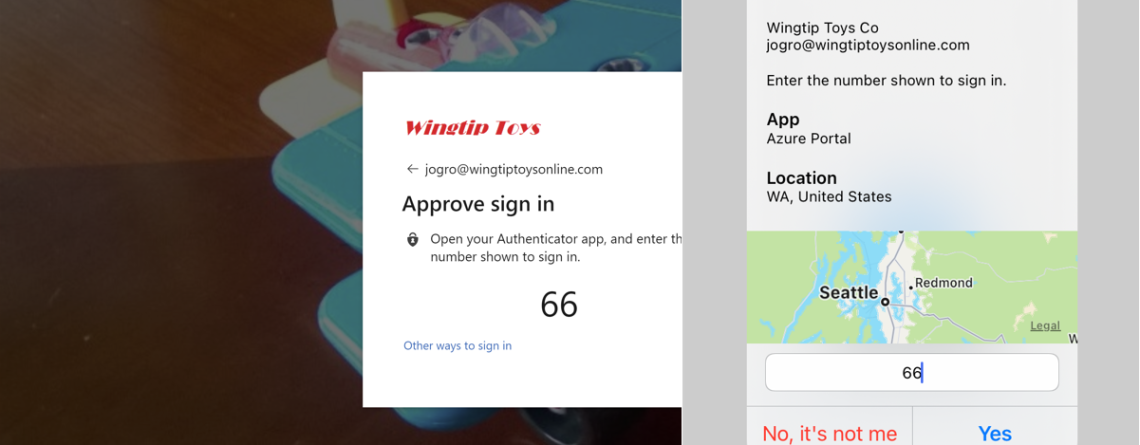
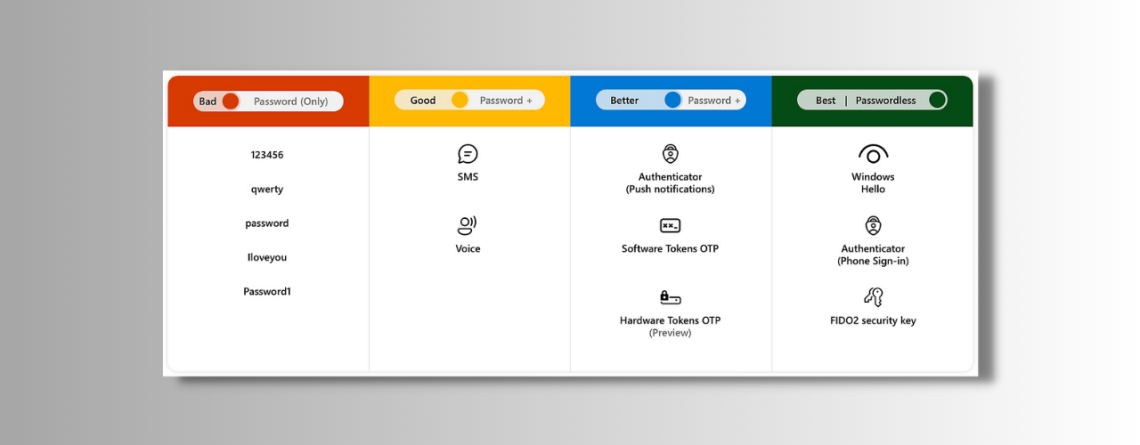
In our continuous effort to enhance the security and convenience of connecting to your account, we would like to introduce a useful feature that allows for a faster and simpler, and more secure login experience, password-less multi-factor authentication. You can begin using this method immediately, by following the instructions below. Before changing to this method, you'll need...